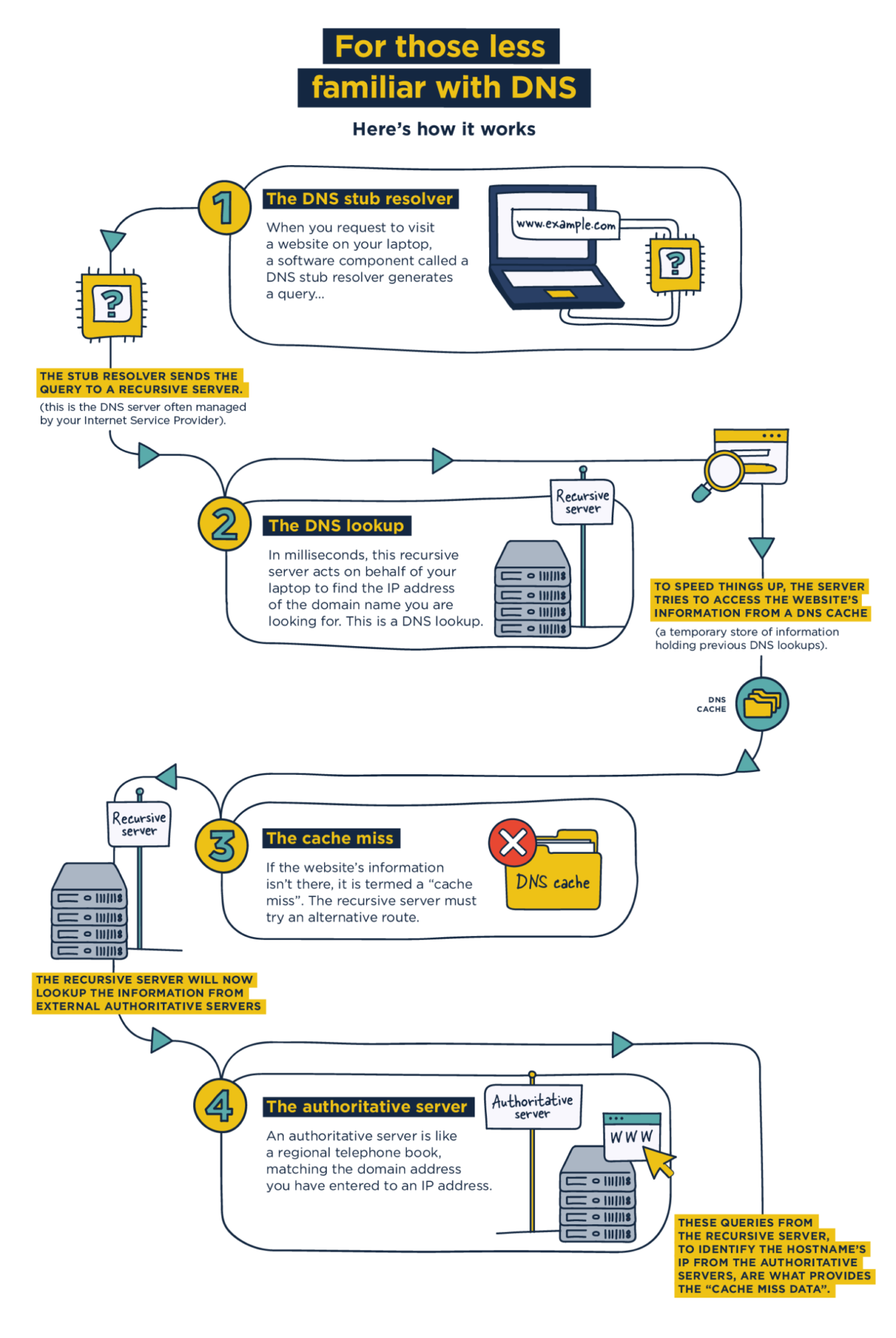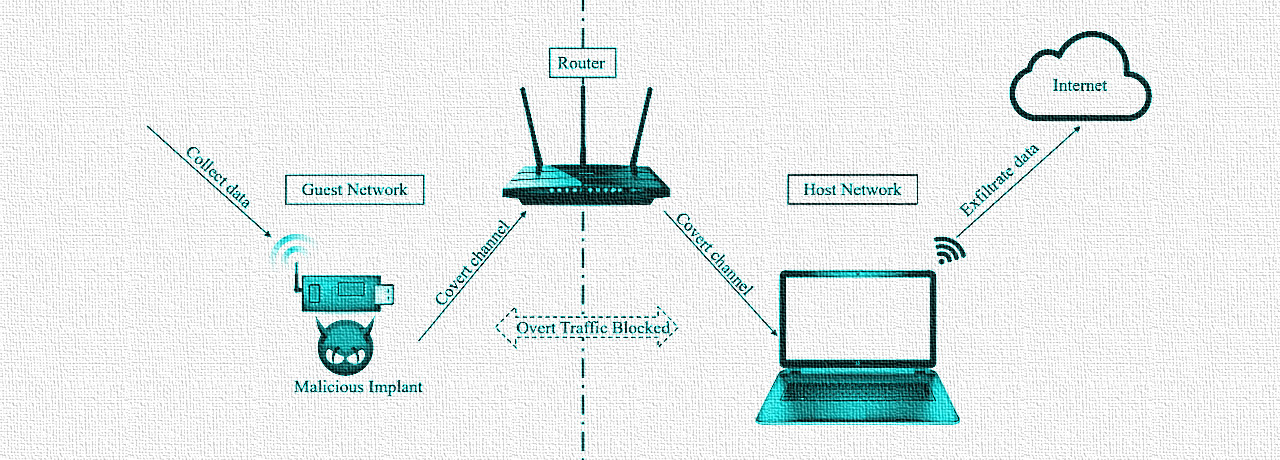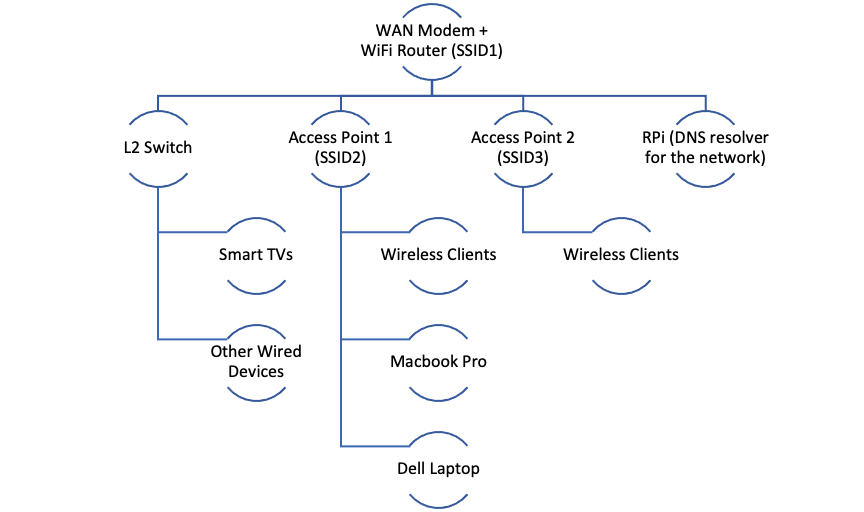
Most clients not connected directly to the Primary router are bypassing PiHole - Help - Pi-hole Userspace

a) Standard configuration: the router acts as a proxy for DNS queries,... | Download Scientific Diagram
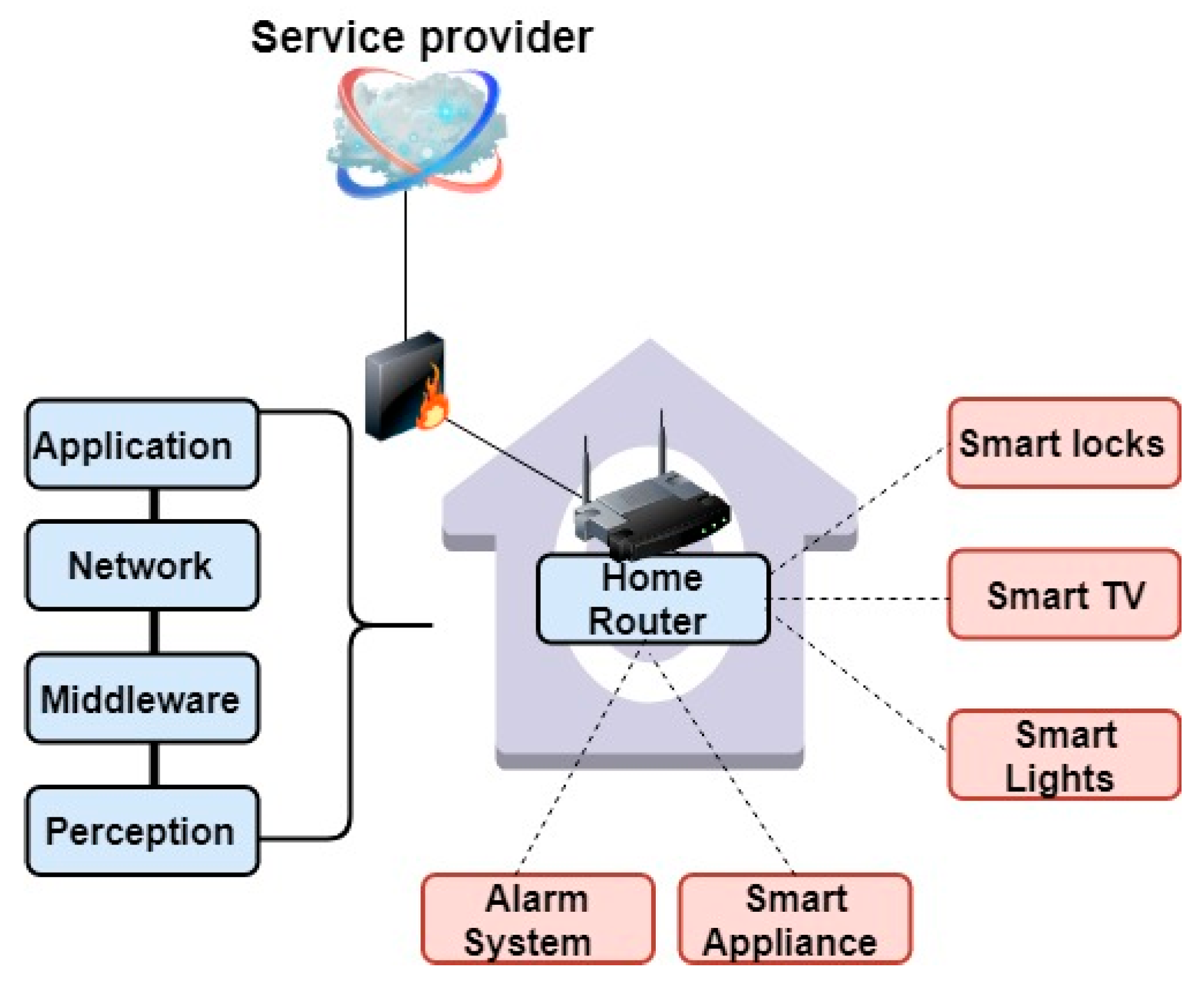
Applied Sciences | Free Full-Text | VPNFilter Malware Analysis on Cyber Threat in Smart Home Network

NETGEAR RAX10 - wireless router - Wi-Fi 6 - Wi-Fi 6 - desktop - RAX10-100NAS - Wireless Routers - CDW.com

Just installed Pi-hole... Wow, is it normal to have > 100,000 queries in less than 15 minutes? : r/pihole









:max_bytes(150000):strip_icc()/google-search-error-captcha-564c72c9e60641d9a1d69a75101d9879.jpg)

![How to remove Search.queryrouter.com [Chrome, Firefox, IE, Edge] How to remove Search.queryrouter.com [Chrome, Firefox, IE, Edge]](https://www.myantispyware.com/wp-content/uploads/2016/12/search.queryrouter.com_search_results.jpg)