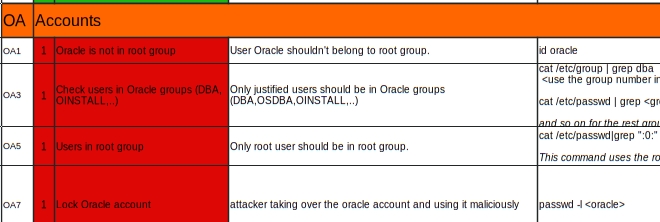
Mariusz Michalowski on Twitter: "The Practical Linux Hardening Guide by @trimstray https://t.co/U7FTGiCkJp #devops #devsecops #kubernetes #cicd #k8s #linux #docker #sysadmin #automation #Azure #infrastructureascode #cloudcomputing #serverless ...

Mastering Linux Security and Hardening - Third Edition: A practical guide to protecting your Linux system from cyber attacks by Donald A. Tevault, Paperback | Barnes & Noble®