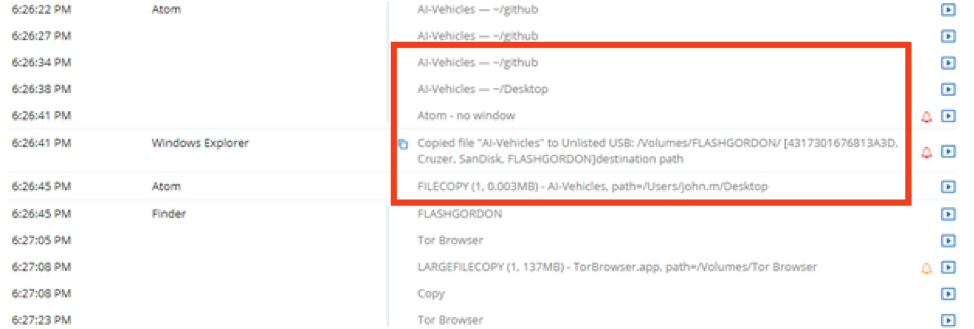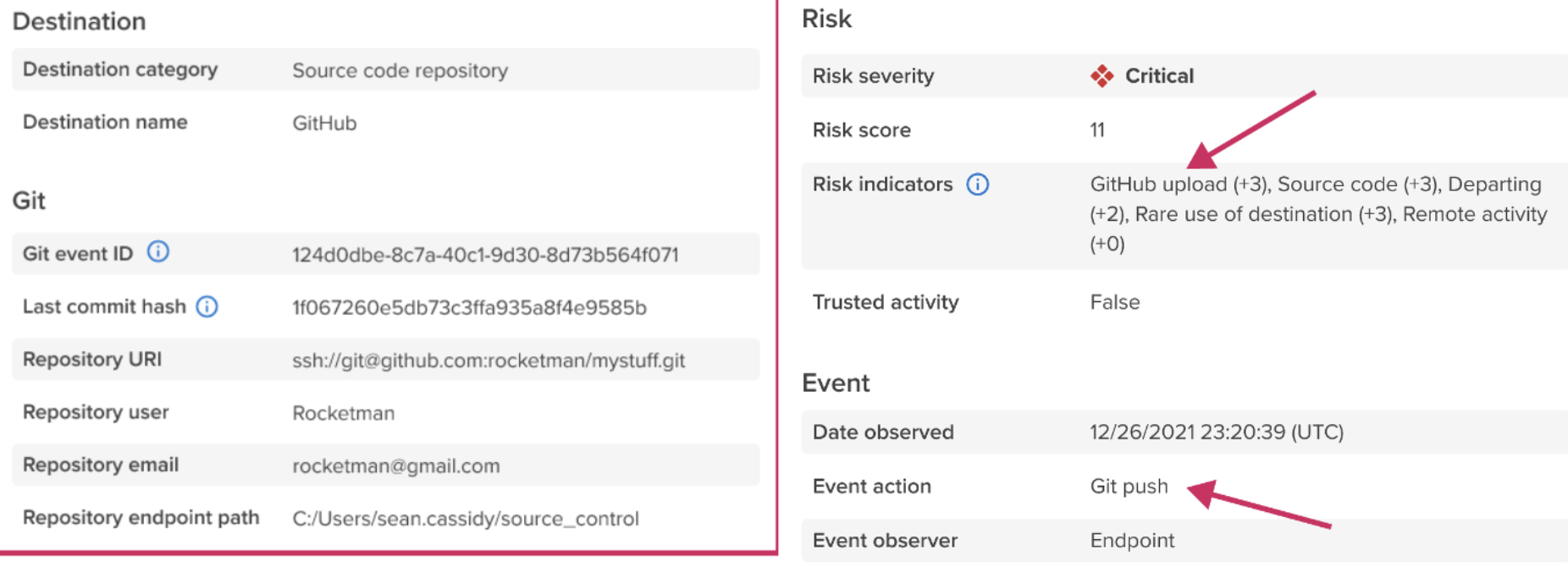
Code42 Incydr Detects Source Code Exfiltration from Git to Unsanctioned Repositories | Business Wire

The Week that Was: Chinese threat actor hit US organizations with a Microsoft cloud exploit. Training code turns out to be malicious in a new proof-of-concept attack discovered on GitHub.
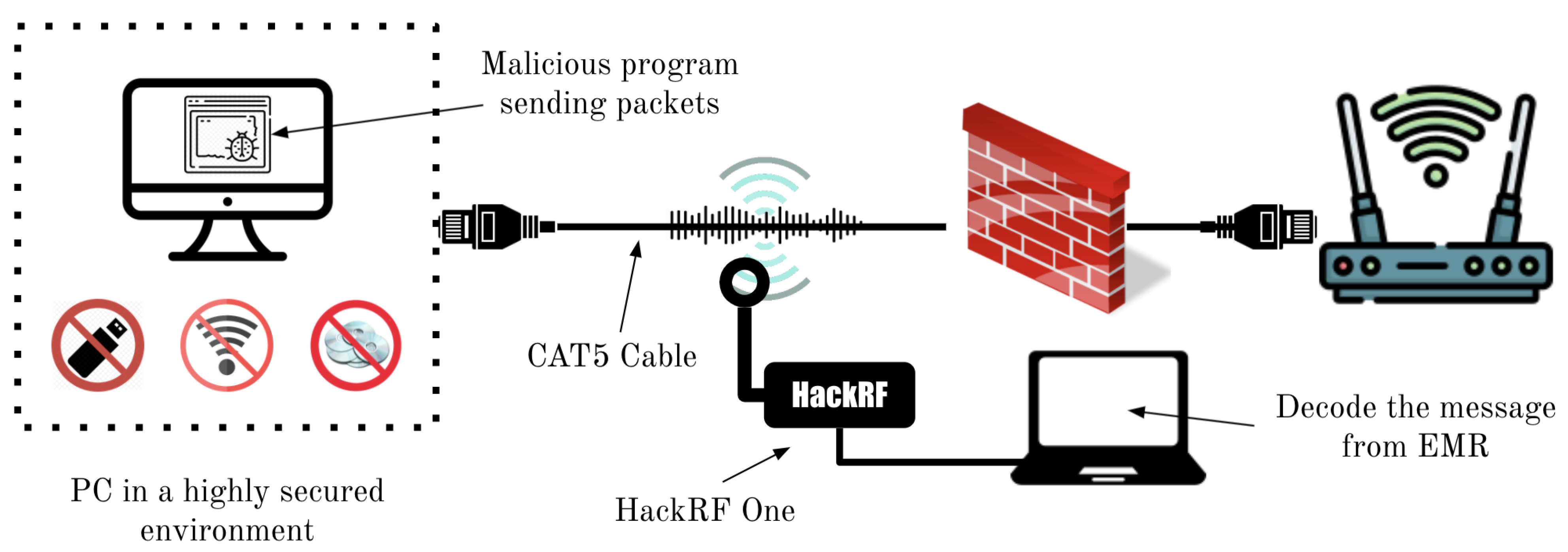
Applied Sciences | Free Full-Text | Data Exfiltration through Electromagnetic Covert Channel of Wired Industrial Control Systems